You saw the struggle: constant breaches, emergency password resets, and sleepless nights. The pain became real—downtime bleeding money, eroded trust, and teams drowning in firefighting mode. So you acted. You brought in pricey consultants, migrated to new services, layered on shiny security tools. But the attacks didn’t stop. They just got smarter, quieter—draining your budget and your team’s morale.
The root cause? It wasn’t your firewall. It wasn’t your cloud provider. It was hiding in plain sight: compromised SSH keys.
Those very keys you deployed for “secure” access? They became your silent liability—reused across machines, left behind on old servers, or exposed in version-controlled scripts. We’ve seen attackers walk right in using those forgotten keys, bypassing every other fix you thought would save you. The truth? Without ruthless control over your SSH authentication, you’re not secure. You’re wide open.
In this guide, we’re not just giving you commands and configs—we’re handing you a battle-tested blueprint:
- How to enable SSH key authentication on Linux VPS
- How to fix the common problems when your key “doesn’t work”
- And how to avoid the devastating mistakes we made, so your team never has to.
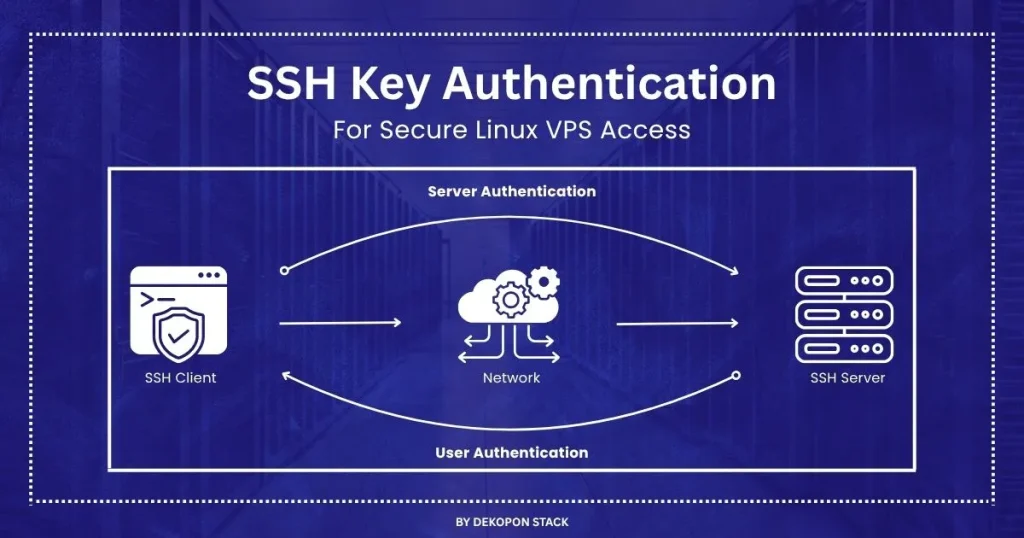
What Is SSH Key Authentication?
SSH key authentication is a secure method of logging into your Linux VPS servers using cryptographic key pairs instead of passwords.
- Public key stays on the server (it’s the lock).
- Private key lives securely on your device (it’s the only key that fits).
When you connect, the server sends a challenge. Your device signs it with the private key. If it matches, access is granted—no password ever exchanged. This eliminates the risk of brute-force attacks, phishing, or keylogging.
Now here’s why it matters:
One of our clients was mid-launch on a Friday night—traffic spiking, orders flying in—when a brute-force password attack locked them out. Their store went offline. Eight painful hours of recovery later, they were back up… but the damage was done: lost revenue, lost trust, lost momentum.
That incident changed everything for us.
Why SSH Key Matters in Linux VPS Servers?
Because brute-force attacks don’t knock—they break in. SSH key authentication stops them cold before they even begin. It doesn’t rely on risky browser-saved passwords that hackers love to exploit. Instead, it gives you total control over who gets in—and who never will. More than just security, it protects your servers, your revenue, and your peace of mind.
How to Configure SSH Key Authentication Setup
Setting up SSH keys is easier than you think. Below is a full guide on how to set up SSH with public key authentication on Ubuntu, Debian, or any Linux VPS servers.
Generate Your SSH Key Pair (Client Side)
ssh-keygen -t ed25519
This creates:
- ~/.ssh/id_ed25519 → Your private key
- ~/.ssh/id_ed25519.pub → Your public key
Use a passphrase for added security.
Add Your Public Key to the Server
There are two ways to add SSH key authentication to your Linux server:
Automatically (Recommended)
ssh-copy-id user@your_server_ip
Manually
cat ~/.ssh/id_ed25519.pub | ssh user@server_ip ‘mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys’
SSH Key Authentication Config on Server
To enable SSH key authentication in Debian, Ubuntu, or CentOS:
Edit your server’s SSH configuration:
sudo nano /etc/ssh/sshd_config
Make sure these lines are present:
PubkeyAuthentication yes
AuthorizedKeysFile .ssh/authorized_keys
Restart SSH:
sudo systemctl restart sshd
✅ You’ve now configured SSH key based authentication on a Linux server.
Enable for Specific Users Only
You can limit SSH key authentication for specific user accounts:
Match User developer
PasswordAuthentication no
PubkeyAuthentication yes
This is helpful when managing multiple users across your server—especially for admin access or restricted roles using public key authentication for admin use cases.
Going Passwordless (Optional)
If you’re confident, go ahead and disable password login:
sudo nano /etc/ssh/sshd_config
Set:
PasswordAuthentication no
Restart:
sudo systemctl restart sshd
⚠️ Warning: Test your SSH key login before doing this. Locking yourself out is no fun.
To re-enable passwords, reverse the above and set:
PasswordAuthentication yes
SSH Key Authentication Use Cases & Tools
SSH key auth isn’t just for terminal logins—it supports remote automation, secure file transfers, and more.
SFTP & FTP
- SFTP (Secure File Transfer Protocol) fully supports SSH key authentication.
- FTP? Not so much. If you’re still using FTP, it’s time to switch.
SSH Key Automatic Login
Once set up, your server can be accessed with a single command:
ssh user@your_server_ip
For convenience, use ssh-agent:
eval $(ssh-agent)
ssh-add ~/.ssh/id_ed25519
Now your key is stored in memory. No passphrase prompts.
This is ideal for:
- Remote deployments
- Remote SSH key authentication
- SSH key authentication for SFTP uploads
Troubleshooting SSH Key Authentication Issues
SSH still asks for a password? Don’t panic—this is common.
Common Fixes
Check Permissions
chmod 700 ~/.ssh
chmod 600 ~/.ssh/authorized_keys
This resolves 90% of SSH key based authentication not working cases.
Validate sshd_config
Look for:
PubkeyAuthentication yes
AuthorizedKeysFile .ssh/authorized_keys
Run this to debug your connection:
ssh -vvv user@server_ip
You’ll see step-by-step logs of the SSH key authentication command line process.
SSH Key Authentication for Different Users or Devices
You can add multiple public keys into a user’s authorized_keys file. This supports:
- Multiple admins
- Multi-device login
- Access control per user
Each key is associated with a different machine or person. To audit, run:
ssh-keygen -l -f ~/.ssh/authorized_keys
This helps in cases like Checkpoint SSH key authentication or other advanced access policies.
SSH Key Management Best Practices
Protect Your Private Key Like It’s Pure Gold
Your private key is your ultimate credential, your digital fingerprint for server access. If it falls into the wrong hands, your servers are exposed, regardless of how strong your other security measures are.
- The Unbreakable Passphrase: Always, always encrypt your private key with a strong, unique passphrase when you generate it. Think of it as a second, uncrackable lock on your most valuable key. Even if your private key file is stolen, it’s useless without this passphrase.
- Isolated Storage: Never store private keys on shared drives, unencrypted cloud storage, or easily accessible public directories. Keep them on secure, local machines that are themselves well-protected. Your private key should reside only where it’s absolutely necessary.
- The SSH Agent Advantage: For convenience and heightened security, use an SSH agent. This allows you to load your private key (and enter its passphrase) just once per session. The key is then held in memory, allowing seamless, passwordless connections without exposing the private key file repeatedly. It’s like having a secure, invisible valet for your keys.
Implement Regular Key Rotation
Just like changing the locks on your home periodically, rotating your SSH keys is a fundamental security hygiene practice.
- Why Rotate? Even with the best security, a key could eventually be compromised. Regular rotation limits the window of opportunity for attackers. It’s a proactive defense against unknown vulnerabilities and dormant threats.
- How Often? Establish a policy – perhaps every 90-180 days, or whenever a team member leaves. This systematic approach ensures no single key remains active indefinitely, reducing long-term risk.
Revoke Compromised or Unused Keys Immediately
This is not a suggestion; it’s a critical emergency response. If a private key is lost, stolen, or if a user no longer requires access, act instantly.
- Zero Tolerance: Immediately remove the corresponding public key from all authorized_keys files on all servers that key had access to. A compromised key is an open door; closing it without delay is paramount.
- Audit Your Access: Regularly audit the authorized_keys files across all your servers. Ensure every public key corresponds to an active, authorized user. Remove any keys that are unfamiliar or no longer needed. Think of it as clearing out old, forgotten spare keys that could fall into the wrong hands.
Use Key-Specific Permissions and Granular Control
Not every key needs access to every server, and not every user needs root access.
- Least Privilege: Grant users only the minimum necessary permissions on a server. If a user only needs to deploy code, restrict their SSH access to only that function, rather than full shell access.
- Force Commands: For automated tasks or highly restricted users, utilize the command=”…” option within the authorized_keys file. This forces the key to execute only a specific command upon login, preventing any unauthorized shell access.
Maintain Strict File Permissions on the Server
The permissions on your .ssh directory and authorized_keys file on the server are non-negotiable. Get them wrong, and SSH will reject your key, often silently for security reasons.
- .ssh Directory (chmod 700): Only the owner should have read, write, and execute permissions.
- authorized_keys File (chmod 600): Only the owner should have read and write permissions.
These tight permissions are SSH’s way of ensuring no unauthorized user can tamper with your access credentials.
Centralized Key Management (For Teams)
If you’re managing multiple servers and a team, avoid the chaos of individual key distribution.
- Automate Provisioning: Use configuration management tools (like Ansible, Puppet, Chef) or dedicated SSH key management solutions to automatically provision and revoke public keys across your server fleet. This eliminates manual errors and speeds up changes.
- Auditing and Logging: Ensure your chosen management system provides robust auditing and logging of all key-related actions. Knowing who added or removed which key, and when, is vital for security and compliance.
Final Thoughts: SSH Key Auth Isn’t Optional
We know what it feels like—that sinking pit in your stomach when something goes wrong, and all eyes are on you. The pressure. The chaos. The fear that one overlooked setting or saved password just opened the door to disaster.
We’ve lived it too. And that’s why we’re not here to preach—we’re here to remind you: SSH key authentication isn’t just a feature. It’s a lifeline.
It’s how you protect the trust you’ve worked so hard to earn, the uptime your customers count on, and the peace of mind your team deserves.
You don’t need another scare to make the switch. You just need to decide: never again.
10 essential SSH Key Authentication FAQs:
1. Why bother with SSH keys if we already use strong passwords?
Because compromised SSH keys create invisible backdoors.
Passwords can be reset instantly, but stolen private keys grant attackers persistent access even after you “fix” other vulnerabilities. Keys require continuous control.
2. How do I know if my SSH keys are compromised?
Audit aggressively:
# List all authorized keys on a server:
sudo ssh-keygen -l -f /home/*/.ssh/authorized_keys
Check for: Unknown keys, outdated algorithms (avoid RSA-1024), and keys from decommissioned employees/servers.
3. What’s the biggest setup mistake?
Lax file permissions:
chmod 700 ~/.ssh # DIRECTORIES
chmod 600 ~/.ssh/* # PRIVATE KEYS & authorized_keys
Incorrect permissions cause 90% of “key not working” issues and expose keys to theft.
4. How often should I rotate SSH keys?
Every 6-12 months (or immediately after staff/contractor offboarding).
Rotate manually:
ssh-keygen -p -f ~/.ssh/id_ed25519 # Change passphrase
ssh-keygen -t ed25519 -f ~/.ssh/new_key # Generate replacement
5. Can multiple team members use one key?
NEVER. Shared keys = untraceable access.
Instead:
- Issue unique keys per user
- Use ssh-agent for individual convenience
- Enforce key comments: ssh-keygen -C “user@device-purpose”
6. We disabled passwords, but attacks continue. Why?
Compromised keys are still active.
Immediate action:
- Revoke old keys from authorized_keys
- Rotate ALL keys
- Add from=”IP” restrictions to new keys:
from=”192.168.1.*” ssh-ed25519 AAA…“`
7. Is using an SSH agent safe?
Yes, if done right:
- Always add keys with ssh-add -t 1h (expire after 1 hour)
- Lock your workstation
- Never use -A (agent forwarding) on untrusted servers
8. How do compromised keys even happen?
Top causes:
- Private keys stored in insecure locations (e.g., team Slack, S3 buckets)
- Developers copying keys to cloud VMs
- Terminated employees’ unrevoked keys
- Malware scanning for id_rsa files
9. What’s the #1 key hygiene practice?
Enforce passphrases:
ssh-keygen -o -a 100 -t ed25519 # Generate with KDF
ssh-keygen -p -f old_key # Add to existing keys
Without a passphrase, stolen keys = instant access.
10. How to restrict what a key can do?
Lock down keys in authorized_keys:
command=”/usr/bin/sftp-only” from=”10.0.1.*” ssh-ed25519 AAA…“`
**Flags like `command=`, `from=`, and `no-agent-forwarding` prevent key abuse if compromised.